Privacy in crypto has always been a double-edged sword. As the Base network grows, so does the demand for truly anonymous payments. Enter Veil. cash – a privacy protocol on Base Layer 2 that leverages zk-SNARKs to enable one-tap, private transactions. Inspired by Tornado. Cash but built for today’s regulatory and technical landscape, Veil. cash is fast becoming the tool of choice for users seeking to shield their financial activity from prying eyes.

Why Choose Veil. cash for Private Payments on Base?
The rise of the Base chain has brought low fees and high throughput to Ethereum users, but transparency comes at a cost: every transaction is public. Veil. cash addresses this by allowing users to deposit ETH or USDC into shared pools, then withdraw those assets from an entirely different address. This process breaks the link between sender and receiver, making it nearly impossible for outside observers to trace your payment flows.
Key advantages:
- Non-custodial: You retain control of your funds throughout.
- zk-SNARKs privacy: Advanced cryptography ensures anonymity within each pool.
- Simplicity: The interface is intuitive enough for one-tap deposits and withdrawals.
This approach doesn’t just benefit privacy maximalists – it’s also critical for businesses, DAOs, and individuals who want to avoid leaking sensitive financial data on-chain.
Step-by-Step: How to Use Veil. cash Private Pools
If you’re new to private payments or just want a refresher, here’s how you can get started with Veil. cash on Base:
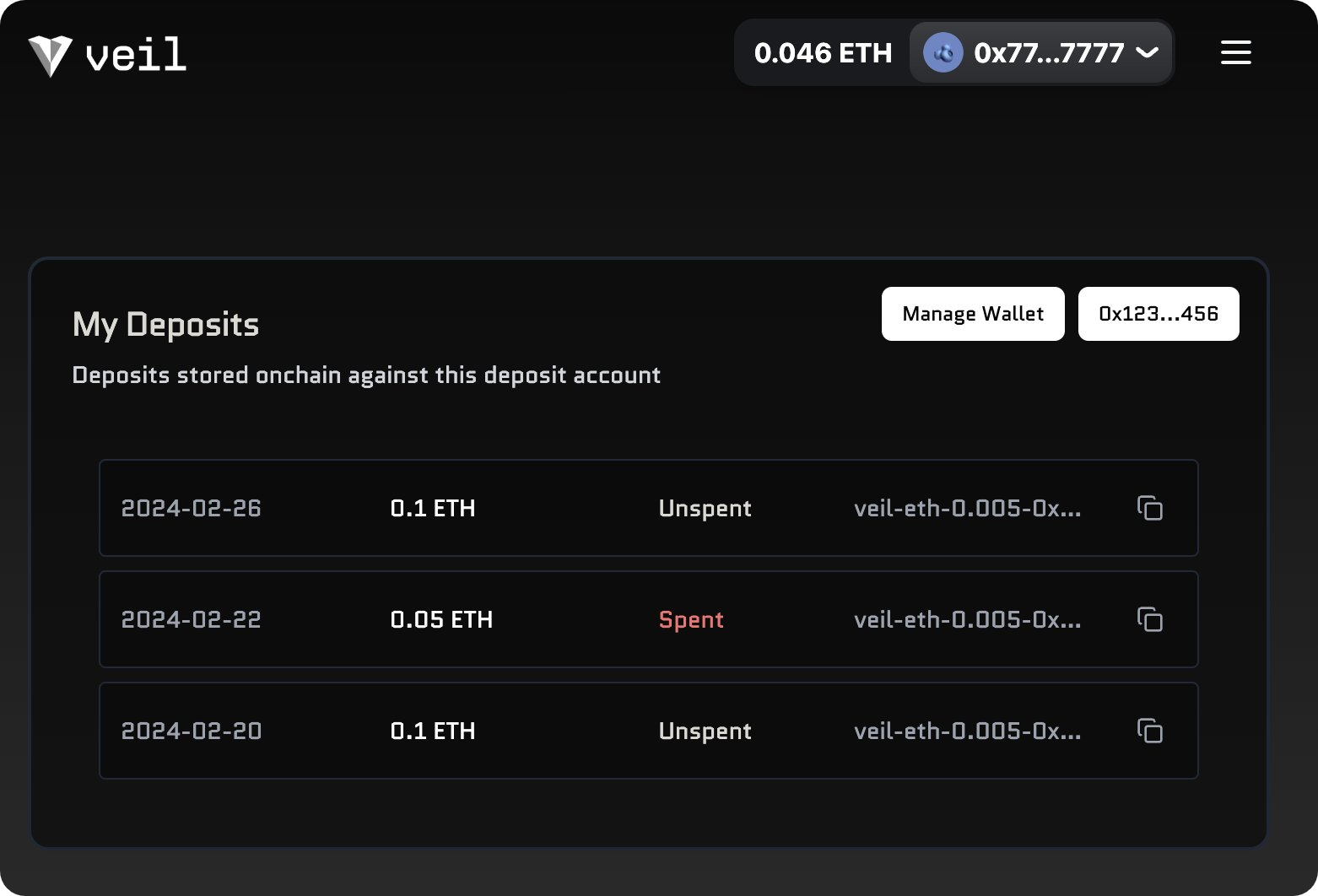
- Connect Your Wallet: Visit veil. cash/app, connect your preferred wallet (such as MetaMask), and switch your network to Base. The dashboard will show available pools and recent activity.
- Select Your Token and Pool Type: Choose between ETH or USDC. Decide whether you prefer a Public Pool (open access) or Verified Pool (requires Coinbase Verify via Ethereum Attestation Service). Verified Pools offer an extra layer of trust among participants.
- Create and Secure Your Secret Note: When you click “Deposit, ” Veil generates a unique secret note. This note is essential for withdrawals – copy it down or securely download it as instructed by the app.
- Deposit Funds: Approve the transaction in your wallet. Your assets are now anonymized inside the pool alongside those of other users.
The Mechanics Behind Anonymous Payments
The real innovation with Veil. cash lies in its use of zk-SNARKs (zero-knowledge proofs). When you withdraw funds from a pool, you provide cryptographic proof that you made a valid deposit without revealing which one was yours. This breaks any direct link between your original deposit address and the withdrawal address.
Best Practices for Maximizing Privacy on Veil.cash
-

Wait for Pool Activity Before Withdrawing: Delay your withdrawal until several new deposits have entered the pool. This helps prevent timing analysis that could link your deposit and withdrawal addresses.
-

Use High-Volume Pools: Choose pools with frequent deposits and withdrawals to blend your transaction among many others, enhancing your anonymity.
-

Split Large Deposits: Break up significant amounts into smaller deposits across multiple pools. This obscures transaction patterns and makes it harder to trace your funds.
-
Vary Deposit and Withdrawal Patterns: Avoid predictable behaviors by changing the amounts and timings of your transactions. This reduces the risk of pattern detection by observers.
-
Withdraw to Fresh Wallets: Always use new wallet addresses for withdrawals that have not interacted with your main address, preventing on-chain linkages.
This method means even blockchain analytics firms struggle to map deposits to withdrawals – assuming you follow best practices like waiting before withdrawing and using fresh wallets each time.
Caution: Experimental Software and Legal Considerations
A word of warning: Veil. cash is experimental and unaudited software. Always exercise caution with significant amounts, stay updated with project news, and ensure compliance with local regulations regarding private payments.
While Veil. cash brings a much-needed privacy layer to the Base network, it’s important to recognize that true anonymity depends on user behavior as much as protocol design. Even with advanced cryptography, careless patterns can erode your privacy. For example, withdrawing immediately after depositing or reusing addresses across different pools could inadvertently link your activity.
To maximize your anonymity when making private payments via Veil. cash, consider these critical operational tips:
Practical Privacy Tips for Using Veil.cash on Base
-

Wait for Pool Activity Before Withdrawing: To maximize anonymity, delay your withdrawal until several new deposits have entered the pool after your own. This helps prevent timing analysis that could link your deposit and withdrawal.
-

Choose Active Pools: Select pools with high deposit and withdrawal volume (e.g., ETH or USDC pools with frequent transactions). More activity means stronger privacy guarantees through larger anonymity sets.
-

Split Large Deposits: Instead of depositing a single large amount, break up your funds into smaller deposits across multiple pools. This makes it harder for observers to correlate your transactions.
-
Vary Deposit and Withdrawal Patterns: Change up your amounts and timing when depositing or withdrawing. Avoid predictable behaviors to reduce the risk of pattern detection by on-chain analysts.
-
Withdraw to Fresh Wallet Addresses: Always send withdrawn funds to a new wallet address that has not interacted with your main address. This breaks the on-chain link between your deposit and withdrawal.
-

Secure Your Secret Note: Back up your Veil.cash secret note securely and offline. Losing this note means you cannot withdraw, while exposing it can compromise your privacy.
-
Stay Informed About Legal Compliance: Veil.cash is experimental and unaudited. Check local regulations before using privacy protocols to ensure you remain compliant with applicable laws.
Remember that the more active a pool is, the greater the anonymity set for every participant. Pools with higher deposit and withdrawal frequency make it significantly harder for outside observers to correlate any single deposit with its corresponding withdrawal. This is especially relevant for those making larger transfers or seeking to avoid targeted surveillance.
Risks, Limitations, and Community Sentiment
Like other privacy protocols, Veil. cash faces ongoing scrutiny from regulators and blockchain analytics firms. The project’s use of zk-SNARKs offers robust protection against most tracking methods, but no tool is completely immune from evolving de-anonymization techniques. Users should also be aware that while Verified Pools add a layer of trust by requiring identity attestation via Coinbase Verify and EAS, this may not suit everyone’s threat model or jurisdiction.
Community sentiment around Veil. cash has generally been positive, especially among privacy advocates who see it as a vital alternative in an increasingly transparent DeFi landscape. However, skepticism remains in some quarters regarding smart contract security and potential regulatory risks, particularly since Veil. cash is still unaudited as of this writing.
Where Does Privacy on Base Go Next?
The launch of tools like Veil. cash signals a meaningful shift in how users approach their financial footprint on Base. As awareness grows around the risks of public ledgers, whether for personal safety or business confidentiality, privacy solutions are likely to see increased adoption despite regulatory headwinds.
Ultimately, using Veil. cash Private Pools for one-tap anonymous payments empowers users to reclaim control over their transaction history without sacrificing usability or speed. For anyone serious about safeguarding their financial data on Base, whether for personal use or organizational treasury management, the combination of zk-SNARKs and smart pool design offers an elegant solution.
If you’re ready to take your privacy seriously on Base, explore verified pools and experiment with best practices outlined above. But always proceed carefully, privacy is only as strong as its weakest link.








